Umbraco CMS High Risk Security Vulnerabilities
DefenseCode’s team of security researchers uncovered a potentially high risk vulnerability in Umbraco CMS.
Umbraco CMS is vulnerable to an arbitrary file upload vulnerability that can lead to Remote Code Execution (depending on server configuration) and Stored Cross-Site Scripting vulnerabilities.
Umbraco CMS is a full featured open source content management system that is flexible enough to handle anything from small campaigns and electronic brochures, to complex applications for Fortune 500 corporations including largest media organizations in the world. It is used by more than 500,000 websites worldwide.
Umbraco CMS is primarily written in C#, stores data in a relational database (commonly Microsoft SQL Server) and is deployed on Microsoft IIS.
Vulnerability Description
DefenseCode ThunderScan® SAST was used to analyze the Umbraco CMS source code, with default scan configuration. DefenseCode ThunderScan® is a SAST (Static Application Security Testing, WhiteBox Testing) solution for performing extensive security audits of application source code. ThunderScan® performs fast and deep accurate analysis of large and complex source code projects delivering precise results and low false positive rate.
ThunderScan® identified the following code logic as vulnerable:
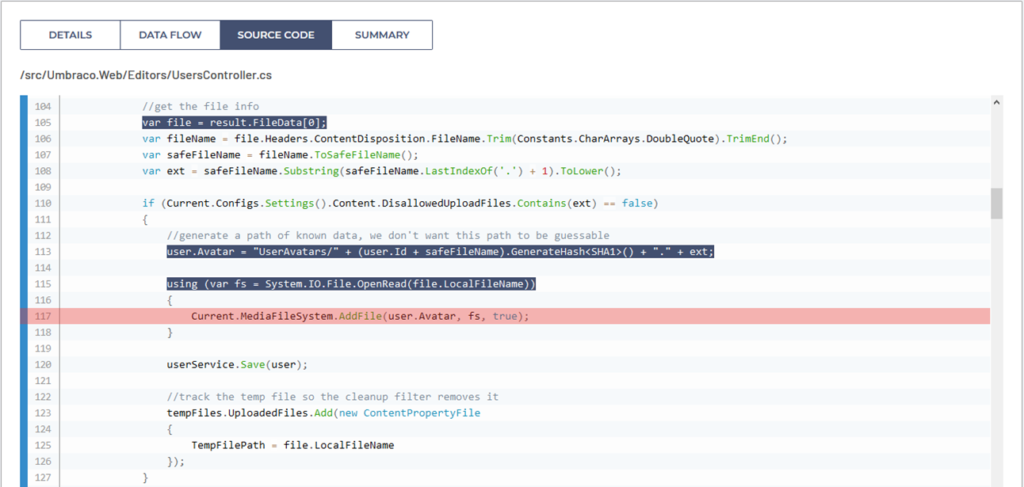
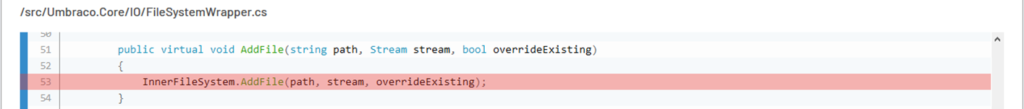
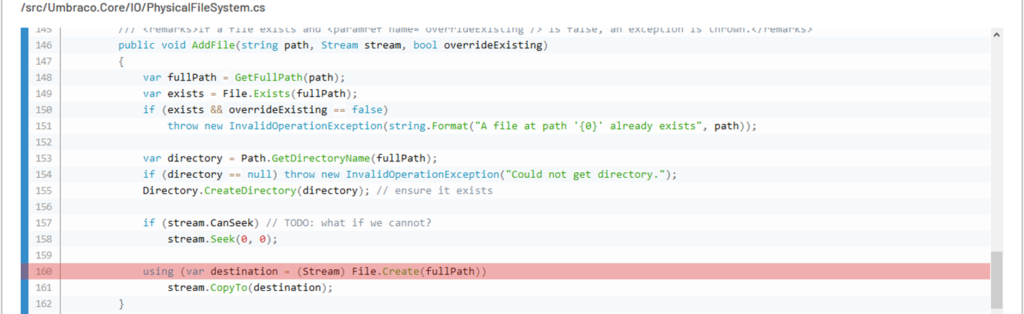
The above logic is related to user avatar image uploads within the user profile (Source code file: /src/Umbraco.Web/Editors/UsersController.cs)
Due to a default scan configuration, the analysis with ThunderScan® did not take into the account custom input sanitization methods such as ToSafeFileName() , a string extension method used to prevent any filename manipulations that would allow for path traversal attacks, or file extension blacklisting checks against the DissallowedUploadedFiles list.
However, blacklist approach to the prevention of potentially dangerous files prompted deeper inspection of the application logic. The default list of disallowed extensions is defined in umbracoSettings.config file as:
<disallowedUploadFiles>ashx,aspx,ascx,config,cshtml,vbhtml,asmx,air,axd,swf,xml,xhtml,html,htm,php,htaccess</disallowedUploadFiles>
Due to this approach, an attacker can resolve to extensions such as .wsdl, .xsl, .xsd and other XML based file types that will be served inline by Microsoft IIS and can contain malicious JavaScript code that can be executed by the victims browser, to effectively perform Stored Cross-Site Scripting attacks in default deployments of Umbraco CMS.
Cross-Site Scripting (XSS) attacks are a type of injection, in which malicious scripts are injected into otherwise benign and trusted websites. XSS attacks occur when an attacker uses a web application to send malicious code, generally in the form of a browser side script, to a different end user. Flaws that allow these attacks to succeed are quite widespread and occur anywhere a web application uses input from a user within the output it generates without validating or encoding it.
An attacker can use XSS to send a malicious script to an unsuspecting user. The end user’s browser has no way to know that the script should not be trusted and will execute the script. Because it thinks the script came from a trusted source, the malicious script can access any cookies, session tokens, or other sensitive information retained by the browser and used with that site. These scripts can even rewrite the content of the HTML page.
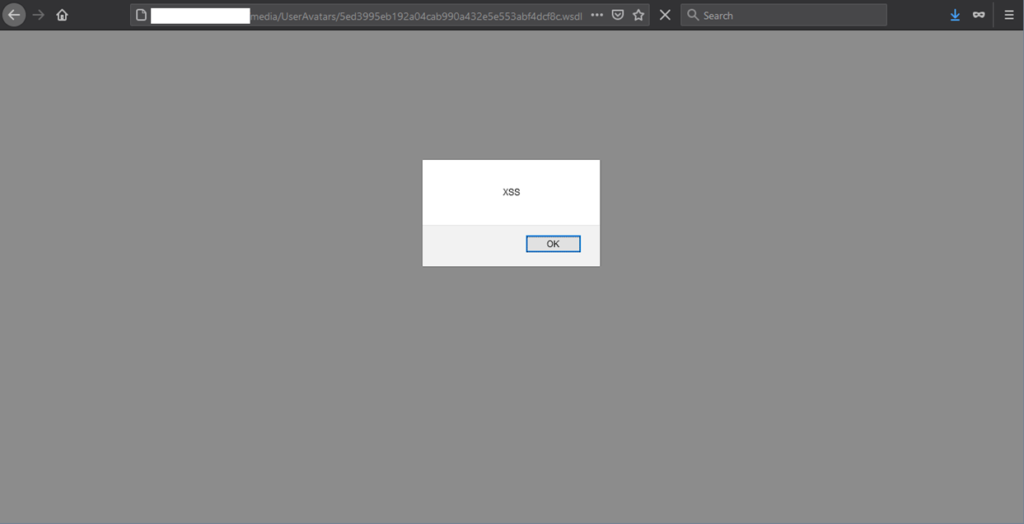
This may be confirmed on the live instance of Umbraco CMS by submitting a POST upload request to the /umbraco/backoffice/UmbracoApi/Users/PostSetAvatar?id=1 endpoint. The extension used for the proof of concept file was .wsdl, with the following content:
<defensecode:script xmlns:defensecode="http://www.w3.org/1999/xhtml">alert('XSS')</defensecode:script>
Proof of Concept JavaScript execution upon visiting the URL of an uploaded file can be seen below:
In case the server supports Classic ASP, uploading .asp files can lead to remote code execution. This occurrence is not uncommon due to the need to support legacy applications hosted on the same server. The same can be said for servers with enabled HTTP Activation feature of WCF Services where .xamlx file uploads would be used for the same attack.
The vulnerability has was been reported to vendor on November 22, 2020, when the latest release of Umbraco CMS was at version 8.8.2. The report has been acknowledged by Umbraco security team on November 25, 2020. Only a single potentially dangerous extension has since been added in the default disallowed extensions list: xamlx.
This leaves the latest current version (8.12.1, at the time of this blog post) still prone to stored cross-site scripting attacks as well as potential remote code execution through Classic ASP files.


